1Password is a popular password manager by AgileBits. It’s much more reliable and user-friendly than LastPass, and has a $60/yr family plan1, so it’s what my family uses to keep track of and share credentials.
Unfortunately it has a couple of design problems that AgileBits does not feel should be fixed.
To be clear up front: These are not critical vulnerabilities. They do not allow strangers to read your passwords. I still use 1Password, and am not recommending most people stop using them, only understand these limitations.
Family Organizer Vault Takeover
Users of 1Password can create additional vaults. This is how users share stored items (i.e. login information) between accounts: Create vault, share vault with other user, move Netflix password into shared vault.
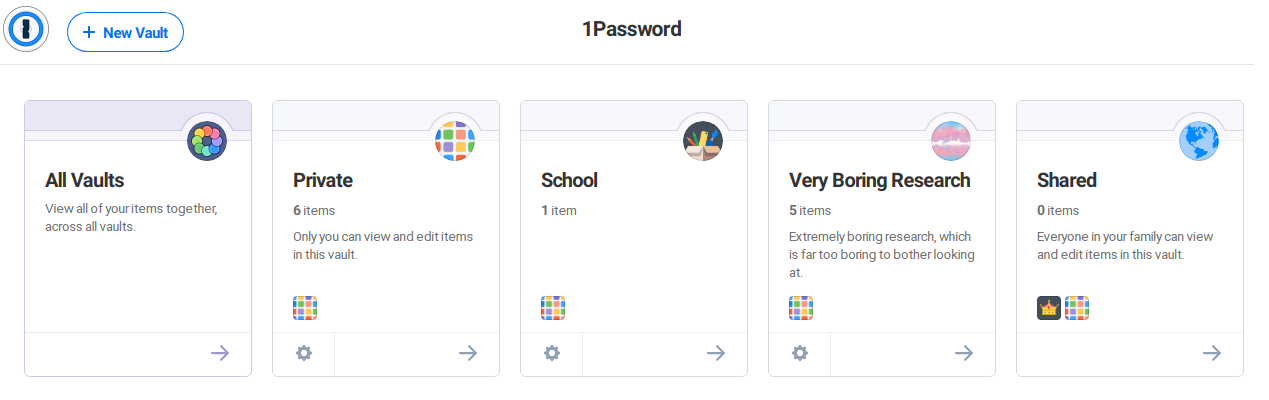
This feature also enables separation of stored items between personal, school, work, and alternate identities. It’s useful to be able to put some things away by switching vaults or removing some vaults from All Vaults when traveling (see also: Travel Mode), hosting a screenshare, or in some physical environments (work, school, church).
The Problem
What isn’t mentioned anywhere in the vault creation process is that if you’re using a family plan the family organizers can add themselves to these additional vaults. That information is only shown on the easily missable Vault Details page, and isn’t even clear in their documentation.
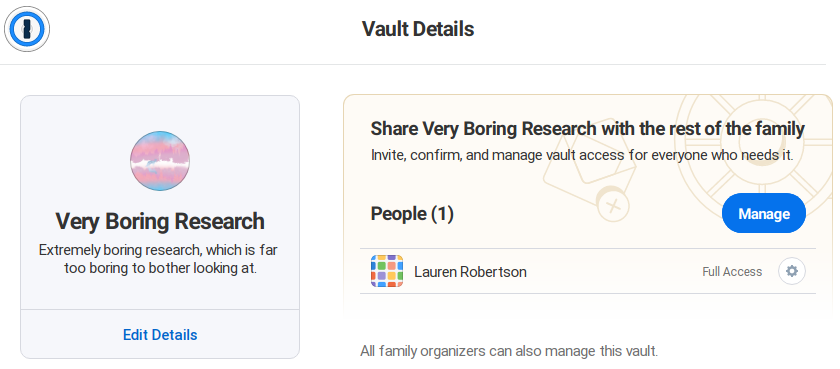
I first discovered this when I noticed I could add myself to a vault shared between my parents and grant myself full permissions. I wrote to their support in 2019 asking if this was intended and how to create a vault organizers couldn’t add themselves to. Their first response actually said that family organizers “cannot manage any of your vaults unless they have explicit permission to that vault”, which would be great if not demonstrably untrue. When asked for clarification, I was informed that only the default vault named “Private” is inaccessable, and all others can be accessed by family organizers.
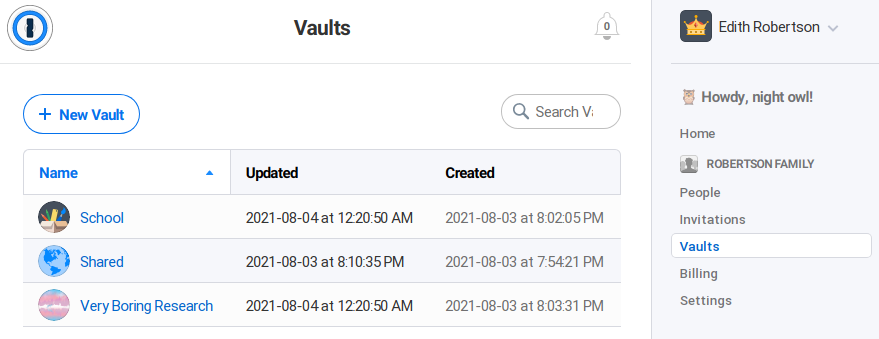 Family organizers can see all secondary vaults created by family members.
Family organizers can see all secondary vaults created by family members.
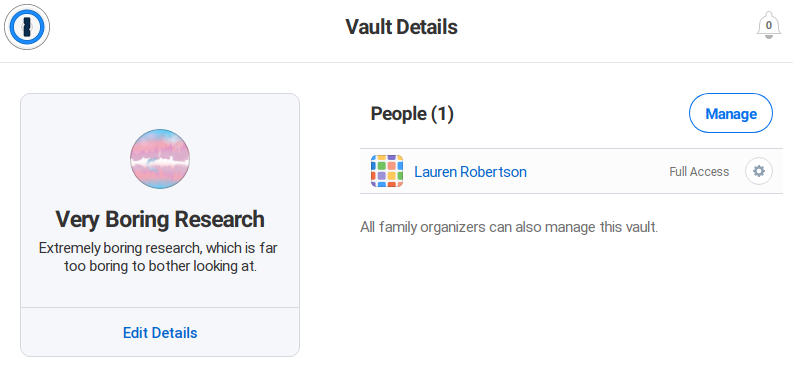 They can see the details, delete the vault, or manage its users.
They can see the details, delete the vault, or manage its users.
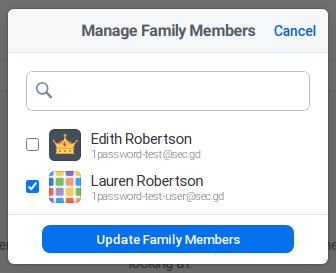 Just a checkbox to gain access.
Just a checkbox to gain access.
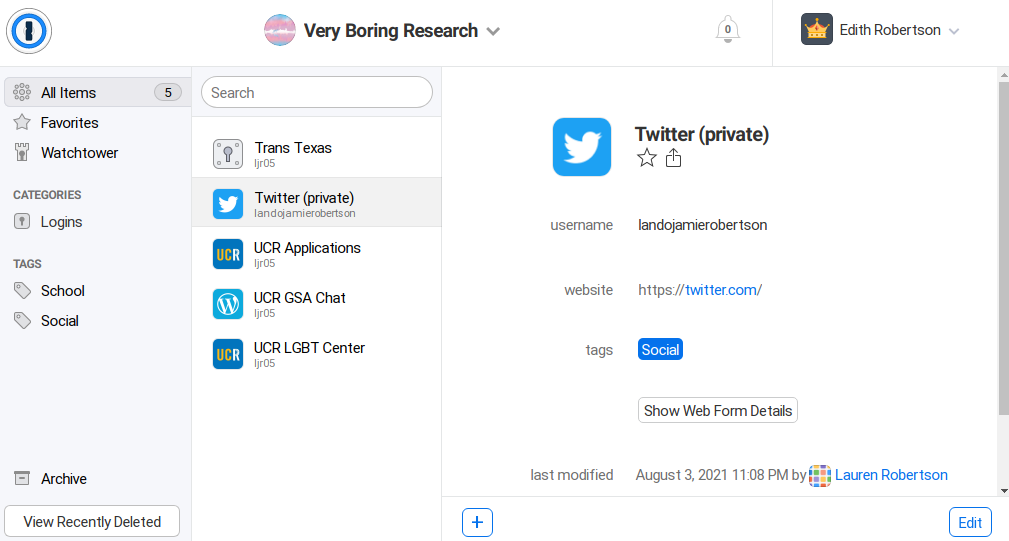 I wonder what they’re hiding from me? Luckily, I have no morals, so I can find
out without having to interact with my child.
I wonder what they’re hiding from me? Luckily, I have no morals, so I can find
out without having to interact with my child.
When I add myself to a vault this way, there are no notifications, confirmations, or logs2. I can add myself, create a backup of the entire vault, and remove myself, and the authorized users would never know.
At best, this makes vaults useless for many situations. I’m contractually prohibited from sharing some credentials with anyone else, so if I add another family organizer as best practice suggests, I can no longer separate work credentials using a vault.
At worst, this could allow a parent to violate a child’s privacy in unexpected ways, or an employer to violate an employee’s3 - not just revealing the sites used but directly and unauditably granting access to them.
If this was clear to users, I would be disappointed, but I wouldn’t be writing this post. The problem is that it’s not - it’s unexpected in the most unpleasant way from a password manager.
Potential Mitigations
Minimum
Transparency. Make clear in the vault creation flow that family organizers can gain access to it. Send a notification and/or email to authorized vault users on membership changes.
Preferred
Cryptographic and server control. Do not encrypt vault keys for anyone not explicitly authorized to have access except in the same manner as account recovery, and do not send the vault data to anyone not explicitly authorized.
Workarounds
- As support suggested to me, use tags instead of vaults, and give up the vault-based features.
- Abandon redundancy and be the only family organizer, and tell your family members that they aren’t able to create vaults you don’t have access to.
- Use only individual accounts, giving up the family plan discount and group-based features.
Leaking Metadata to Network Admins
Unlike the first, this problem applies to all accounts - Individual, family, and business, whether subscription or app-licensed. When the 1Password app or browser addon shows vault entries, it shows an icon for each website. Instead of being saved in your vault, they’re requested from the server when they’re shown. The Windows desktop app appears to cache them, but the browser addon appears to request them again each time they’re shown.
Normally the privacy impact of this is what they describe on their rich icon privacy page: Your network sees that you use 1password, and the CDN sees your IP address and the domain you’re requesting an icon for. This isn’t ideal but is acceptable to most users. Others can disable it, assuming they notice and understand the setting, and that they’re not using the browser extension, where the setting doesn’t exist.
The Problem
Many schools and companies use SSL/TLS inspection (TLSi) either to restrict
what content is available from the network or to ensure sensitive information
is not being sent out of the network. TLSi works by requiring every device to
add a new trusted certificate authority, and then signing a new TLS certificate
for every site a device tries to contact. The end result is that the user sees
the normal 🔒 https://... in their browser and everything works normally, but
when their traffic reaches the system performing inspection, it’s decrypted,
scanned, potentially logged, and then re-encrypted and passed along.
This means that every time the user clicks the 1Password button, opens their vault, or has the autofill popover show up, their school or workplace will get logs like these:
![]() SSL added and removed here! :)
SSL added and removed here! :)
Depending on the domain and the aggressiveness of web filters, this may even trigger automated alerts to administrators, including the wildly inappropriate “adult content” classification for LGBTQ+ resources. These alerts are often passed along to parents or supervisors for disciplinary action.
When I contacted support about this, I was referred to their rich icon privacy documentation page.
Users expect password managers to do everything possible to keep their contents, including the metadata, private. In situations where an unavoidable environment like work or school may disagree with parts of a 1Password user’s personal life, this expectation is put to the test, and its failure may have significant consequences.
Potential Mitigations
- Ideally, store images encrypted for the user, encrypt requests. This would increase server disk space needs and load. Alternatively:
- Pin the keys of the CDNs so inspection devices don’t see the requested URLs. This slightly degrades the user experinece, but I feel this is a more than acceptable tradeoff in those cases. Unfortunately this probably isn’t possible in the browser extension.
- Implement a setting to disable rich icons in the browser addon
- Obfuscate, e.g. encrypt images with
hash(domain), request withhash(hash(domain)). Defeats trivial observation, but doesn’t prevent confirmation of known domains. - Cache icons for as long as possible to reduce the amount/chance of information leaking.
Workarounds
- Don’t use 1Password in TLS-inspected environments.
- Disable vaults containing sensitive domains when in a TLS-inspected environment, if the above issue with vaults doesn’t preclude their use.
- I haven’t found a way to block the requests with uBlock Origin or even uMatrix, so… Accept the risk, or disable the browser addon when in TLS-inspected environments.
- Disable rich icons in settings, or don’t use the apps either in TLS-inspected environments.
- Ideally, use a VPN like Wireguard to escape TLS-inspected environments and never install new trusted certificate authorities regardless of this issue.
1Password CLI Leaks
Added 2021-09-29
As reported by Graham Christensen, the 1Password CLI tool (op) exposes
sensitive information including passwords to all other users and processes on
your system through command arguments.
AgileBits are aware of this and consider it not a problem.
“Luckily”, unlike other password managers’ command line tools, op is quite
difficult to use as a human - its interfaces almost seem to be intended as an
API instead of for direct use.
Read more about this problem in Graham’s twitter thread
Mal Whining
While I’m writing about 1Password, I may as well mention the other things that I’d like to see changed.
Inactive Account Management
As described in the whitepaper, there is a mechanism for assisting family members or team members with vault recovery. A simplified explanation is that the server holds a copy of each family member’s vault key, encrypted so only family organizers can access it. If I initiate recovery for my mother’s vault, she receives an email allowing her to create new keys. Once she’s done so, the server gives me the encrypted vault key (but not the vault data) so I can re-encrypt it with her new public key.
This is about as good as I can ask for a user-friendly recovery system, but I would like to see the ability to configure my account to grant access to specific vaults to a family member if I don’t sign in for some number of months and don’t respond to emails or text messages.
The cryptographic features are already there, this mode would just skip the email confirmation, and the server would grant vault data access as well.
Backups
As mentioned, the Linux app is not feature-complete, and there’s no way to grant access to vaults automatically if I’m run over by a bus. It would be great if the ability to make backups was prioritized for either Linux or the web interface.
Container Incompatibility
Firefox has a great feature called Container Tabs that allows easy separation of multiple accounts, identities, or contexts. I use it extensively to keep work accounts in one container, personal in another, and stay signed out in the default container.
When selecting “Open & Fill” in the 1Password extension, it creates a new tab in the default container, and uses that to navigate to the site. This means the only way to sign in to a site in a chosen container is to copy the link and paste it into a new container tab manually.
I brought this up on their forum in 2018, and for a few versions the extension would reuse the existing new container tab if present, but then it stopped working again, and they still haven’t fixed it.
If they wanted to, they could build neat integrations, like having the extension always open a login (or even just anything in a particular vault) in a configured container. For now, all I ask is to not override my choice.
Getting to the web interface
Nearly all of the management of vault items and account settings is done through either the web interface or one of the applications. The Linux app is currently in beta and not feature-complete, and typing on a phone is tedious, so I’m left with the web app. (2022 update: The linux app is improving, and I can access that by clicking the icon in my taskbar, but this annoyance remains for those who don’t use the desktop app.)
To access the web app, I can either go to the site and enter my password again, or I can have the extension open it alreay authenticated.
For some reason, the only way I’ve found to do this is to click the extension’s icon, click the settings gear, click Settings, scroll to the bottom, click one of the vault names, and then navigate where I need to go in the web interface.
Could we get a link next to Settings that’s just “Manage from web”?
-
1Password is also available without the web/sync features as a one-time purchase. I expect everything described here to apply to that use as well, but it’s not what AgileBits are pushing, and I don’t want to buy it to test. ↩︎
-
Business plans may expose audit logs. I don’t have one to test, but I would be surprised if those logs were made available to normal users. ↩︎
-
This is less clear, as many employers have policies stating employees have no expectation of privacy. I would argue that employees should be reminded of this at every point where it might be important. ↩︎